Choose the penetration testing package that best suits your needs
Attack Surface
A basic level of test to simulate the methods of an opportunistic hacker. Quickly uncover common application security weaknesses found during an automated vulnerability assessment.
Authenticated
This more in-depth application test is ideal for organizations that need to model an attack by a more determined cyber-criminal with stolen credentials.
Test activities in scope:
| Get a quote | Get a quote | |
| Data-in-transit & data storage protection | ||
| Key management & algorithm logic | ||
| Information disclosure | ||
| Injection vulnerability (XSS, SQL, HTML, XML, JSON, OS command) | ||
| Path traversal | ||
| Object identifiers | ||
| Local and remote file inclusion | ||
| Stack-based bounds checking | ||
| Compliance reporting for SOC2, ISO 27001, PCI-DSS, HIPAA, etc. | ||
| Authentication bypass | ||
| Password policy | ||
| Login limitation policy | ||
| Session management | ||
| Hijacking | ||
| Predictable identifiers | ||
| Reply and expiration attacks | ||
| Privilege escalation | ||
| Horizontal access | ||
| Cryptographic algorithm strength | ||
| Key management | ||
| Injection vulnerability (XSS, SQL, HTML, XML, JSON, OS command) |
Attack Surface
Infrastructure test to identify security vulnerabilities. Simulates opportunistic hacker attack patterns.
Authenticated
Infrastructure test simulating a hacker attack after breaching the perimeter or obtaining valid user credentials.
Test activities in scope:
| Get a quote | Get a quote | |
| Validate and exploit known vulnerabilities | ||
| Network segmentation | ||
| Insecure network protocols | ||
| MITM attacks | ||
| VLAN/ACL issues | ||
| Credential capture | ||
| Compliance reporting for SOC2, ISO 27001, PCI-DSS, HIPAA, etc. | ||
| Password cracking | ||
| LDAP/AD security | ||
| System & network privilege escalation (Vertical / Horizontal / Adjacent) |
Fully scoped penetration test
We can customize our penetration testing services to meet your specific needs. Our range of services includes thorough and targeted testing for any situation.
- ✓ Cloud
- ✓ Mobile app
- ✓ API
- ✓ Red teaming
- ✓ Web app
- ✓ Social engineering
- ✓ Infrastructure
We will conduct a comprehensive penetration test that mimics a focused attack on your company. Our skilled testers will employ all the methods and resources utilized by actual cyber criminals to achieve your desired outcomes.
All our pen tests include


Pen testing certificate

Report with prioritized threat list

Dedicated account manager

Expert remediation advice
Our Penetration Testing Team
Our organization is committed to developing high-quality cybersecurity talent, and staying ahead of the constantly changing threat landscape. With a team of more than 30 highly skilled penetration testers, each with significant experience in conducting a variety of penetration tests, we offer advanced and sophisticated services. Our team members hold industry-standard certifications, demonstrating our firm dedication to delivering exceptional quality and service.

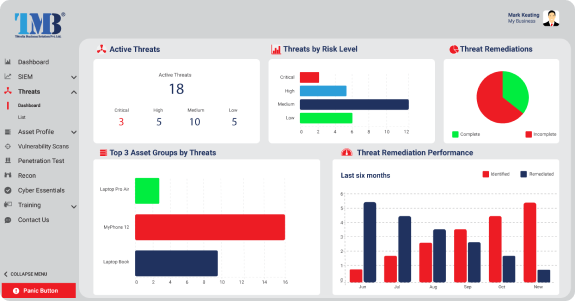
Smart Report Delivery and Remediation Advice
Upon completion of your penetration test, the findings outlined in your report will be uploaded to our secure platform. The report will contain a comprehensive breakdown of all vulnerabilities discovered during the test, accompanied by actionable remediation advice.
As an added benefit, each identified vulnerability will be automatically added to your Threat Dashboard, in addition to being included in the PDF report. This feature will enable you to swiftly identify, prioritize, and take appropriate action to address the threats that are impacting your organization.
Why choose TMBS as your penetration testing company?

Competitive pricing
Penetration testing is affordable and useful for businesses of any size.

Dashboard reporting
Monitor report results, rank risks, and obtain solutions through TMBS.

Certified experts
Our pen testers are certified by CREST and OSCP.

Free vulnerability scans
Get free vulnerability scans with our 12-month pen test package.