The global average cost of a data breach is $4.35 million
IBM & Ponemon Report, 2022
Low-touch, high-impact cybersecurity defence

Real-time protection
Real-time SIEM-based monitoring combined with security expertise from our 24/7 SOC means we detect, analyze, and stop attacks in seconds.

Seamless security
TMBS MDR integrates with your existing security teams and tooling, for 100% security coverage.

Rapid time-to-value
Start protecting your business in hours, not weeks, with expedited onboarding and lightning-fast remediation.

Threat hunting
Seasoned security professionals use the latest technology and intelligence to proactively search for hidden threats.
Accurate detection, quick remediation
Protect your data and assets from threats that evade your other security controls with MDR services from TMBS.

Free your staff & budget
MDR can eliminate the burden of security management, freeing your staff and your budget.

Stop alert fatigue
Say goodbye to meaningless alerts and get actionable, reliable remediation advice.

Comprehensive visibility
Maintain a complete view of your business data and assets to quickly detect threats.

Security integration
Our MDR service enhances your existing security investments.

Incident response
We're here to support you through every stage of the incident lifecycle.

Prevent data breaches
Meet your compliance-driven monitoring requirements and proactively avoid data breaches.
What can TMBS MDR service do?
Our MDR service has been engineered for power and performance, so we’re able to react quickly to all security threats, including:
- Proactive phishing protection
- Malicious website blocking
- USB blocking
- Malicious IP blacklisting
- Hosting and device isolation
- Isolate suspected breached users
- Protect remote staff as if they were on-premises
TMBS MDR integrates with your security stack, so you can get more from existing investments. Your security implementations are monitored and leveraged to provide strong defenses.
Discover the TMBS difference
TMBS MDR is a low-touch, high-impact managed service that solves the problem of hiring expensive in-house security teams.
- ✓ Our powerful SIEM platform ingests any logs from any source at any volume
- ✓ Service is aligned to the cyber kill chain and operates to SANS incident response best practices
- ✓ Tried-and-tested runbooks set a strong security baseline
- ✓ Start seeing value quickly with a fast on boarding process
- ✓ Endpoint tooling proactively isolates assets to stop attacks in progress
- ✓ Built to be effortlessly scalable to grow with your businesses
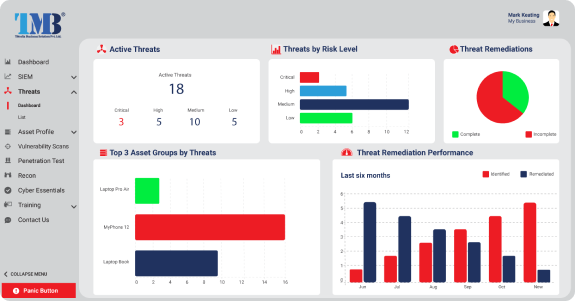
Powerful security tools included as standard
Our MDR offering shall be furnished via the TMBS comprehensive Software as a Service (SaaS) platform, replete with a multitude of robust and potent threat management utilities, such as vulnerability scanning, phishing simulation, and video training.
In addition, our MDR service and any other potential threats shall be meticulously categorized, graded, and overseen through an all-inclusive dashboard, presenting you with a panoramic and thorough appraisal of your entire security terrain.
Your cybersecurity experts
TMBS has revolutionized the field of cybersecurity by spearheading the development of our own sophisticated technology stack, which affords you access to a scalable and expeditious Managed Detection and Response (MDR) platform, complete with real-time intelligence and potent correlation engines. We also take great pride in our knowledgeable and seasoned security professionals, who diligently monitor and safeguard your systems 24/7 from the rapidly evolving threat landscape.
The data culled from our comprehensive suite of solutions undergoes a rigorous process of anonymization and aggregation, ultimately contributing to our proprietary threat intelligence. This cutting-edge research is bolstered by our vast repertoire of commercial and open-source data feeds, ensuring that we remain at the forefront of the cybersecurity protection frontier.